Make Hackers Pass on Your System
Hackers choose obvious vulnerabilities. On the user side, problems stem from outdated applications and OS software, updated but not rebooted PCs, and update testing for compatibility, so that even partially opened doors can invite hacking. For the designer side, however, many simple solutions can take your designs out of the inopportune category of “low-hanging fruit.”
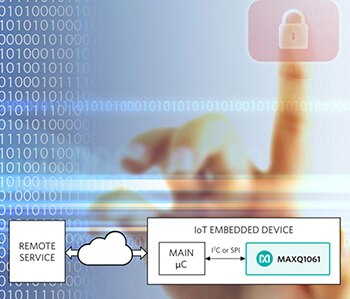 Figure 1: The MAXQ1061 DeepCover Cryptographic Controller is easier to integrate into simple systems compared to TPM 2.0-based solutions. (Image source: Maxim Integrated)
Figure 1: The MAXQ1061 DeepCover Cryptographic Controller is easier to integrate into simple systems compared to TPM 2.0-based solutions. (Image source: Maxim Integrated)
The mere use of multi-factor authentication and sufficient password strength goes far to turn some hackers away. Specifically, the design of IoT devices that are secure enough to be approved to company networks makes sense. And, establishing exactly what can be attached to company networks, provides even greater deterrents. Several other quick and easy solutions will also make you much less of a target. Here are three examples.
Take, for instance, the MAXQ1061 DeepCover Cryptographic Controller from Maxim Integrated (Figure 1). Designed as a companion chip for small embedded devices, this chip uses minimal resources. The easy-to-use and efficient solution is an alternative to chips based on the TPM 2.0 Standard that are difficult to integrate into simple systems, including many of those intended for the IoT. The MAXQ1061 is designed to protect authenticity, confidentiality, and integrity of software IP. Applications include IoT nodes connecting network appliances, PLCs, industrial networking, and embedded devices.
The MAXQ1061 supports highly secure key storage and simplifies certificate distribution. Its high-level functions streamline SSLTLSDTLS implementations and it features several communication-interface options for simple connection to a host processor. Supported cryptographic algorithms include AES, ECC, ECDSA signature scheme, and SHA, and a true random number generator can be used for on-chip key generation. The MAXQ1061 provides a strict necessary set of 40 commands, which helps avoid unnecessary complexity. It delivers a simple access control policy and features that answer most security scenarios for IoT devices.
Taking DeepCover technology even further for such devices as IoT gateways and wireless access points, the MAX32520-BNS+ DeepCover embedded security solutions cloak sensitive data under layers of advanced physical security layers, providing enhanced secure key storage. The MAX32520 delivers an interoperable, secure, and cost-effective solution for trusted embedded systems and communication devices. It incorporates Maxim's ChipDNA physically-unclonable-function (PUF) technology to ward off invasive physical attacks. ChipDNA generates a unique output value that’s repeatable over time, temperature, and operating voltage to cryptographically secure all device stored data including user firmware.
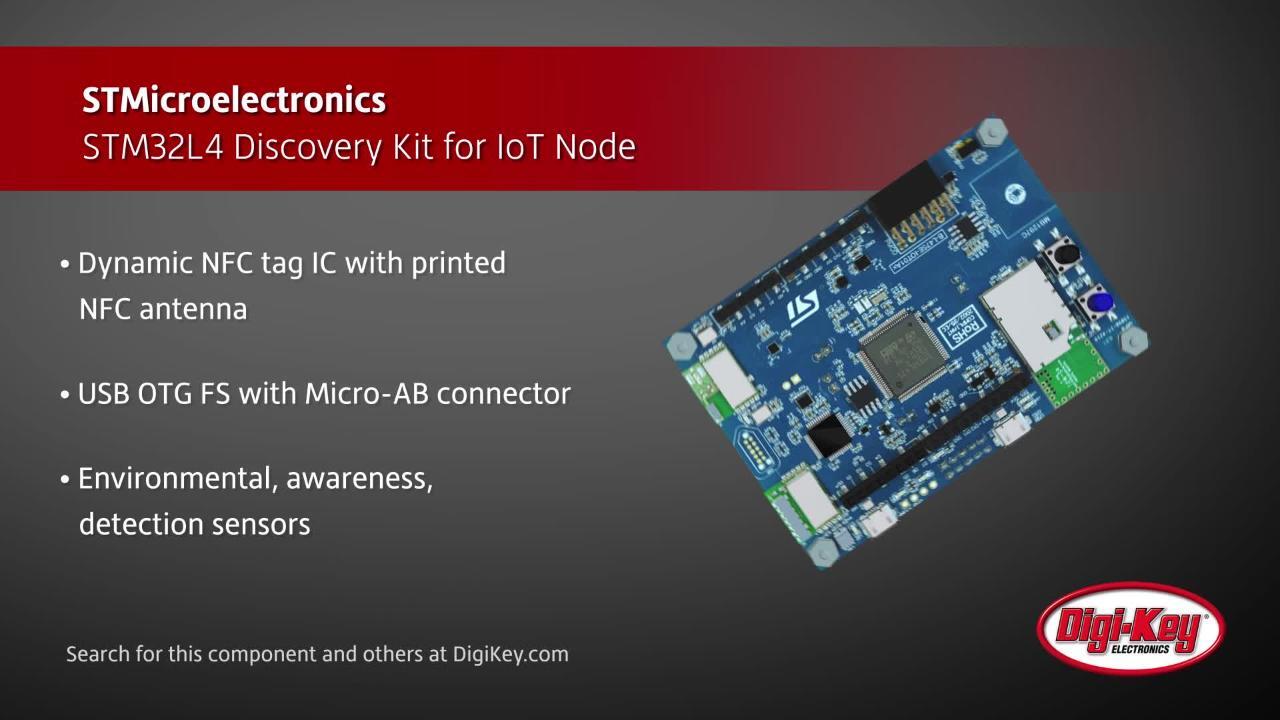
 Figure 2: The STM32L4 combines voltage scaling, ultra-low-power communications for apps connecting directly to cloud servers. (Image source: STMicroelectronics)
Figure 2: The STM32L4 combines voltage scaling, ultra-low-power communications for apps connecting directly to cloud servers. (Image source: STMicroelectronics)
Another solution aimed at IoT Edge devices is the STM32L4 IoT Discovery Kit from STMicroelectronics (Figure 2), which enables the development of applications that have a direct connection to cloud servers. The STM32L4 MCU delivers dynamic voltage scaling that balances power consumption with processing demand and low-power peripherals (LP UART, LP timers). Additional features include 64-Mbit Quad-SPI Flash memory, Bluetooth V4.1, a sub-GHz low-power programmable RF module, a Wi-Fi module, and a dynamic NFC tag with printed NFC antenna. It offers ultra-low-power communications multiway sensing found in the ARM Cortex-M4 core-based STM32L4 and has 1 Mbyte of flash memory and 128 kbytes of SRAM.
Take a stand
There’s a plethora of devices in use in companies, homes, and in the field that have insufficient (read: nearly none) security. The demand for easily updated and secure IoT devices that are not particularly easy to hack is growing exponentially. Finding ways to implement security is a must to protect not only the user’s reputation, but also your own.
Of course, not all designs need to be hidden by 20 layers of the latest and greatest deterrents. Just don’t make it easy for the bad guys. Instead, implement a secure boot process, store keys where they aren’t waiting to be grabbed, and protect memory. Make it as difficult as you can based on your budget, and add in a dose of common sense.

Have questions or comments? Continue the conversation on TechForum, DigiKey's online community and technical resource.
Visit TechForum